Clear And Present Danger: Act Now On Medical Device Cybersecurity

By David Remick, KPMG LLP
The current state of medical device cyber readiness and compliance requires an immediate industrywide call to action. Manufacturers and healthcare providers must collaborate to identify cybersecurity and privacy risks, to plan for mitigation and remediation, and to ensure that all patients are safe and secure.
Cybersecurity attacks against healthcare providers and health plans generate a lot of attention, given the voluminous and sometimes shocking number of patient records compromised. Tens of millions of patient records have been compromised from cyber-attacks against health plans. Meanwhile, some hospitals’ IT systems have been hijacked by ransomware – disrupting operations and posing a great risk to patient care. KPMG’s 2015 Healthcare and Cyber Security survey found that more than 80 percent of health plans and healthcare providers acknowledge that patient data has been compromised, even after significant cyber-related investments. Medical devices represent an attractive target for cyber threat actors, given the vast and growing number of devices in use, interconnectivity of these devices with other systems, and the fact that these devices contain and process sensitive patient information.

Recent medical device innovations have focused on connectivity and enhanced patient experience. Interconnectivity of medical devices has benefits, such as improved clinical effectiveness, but it also introduces new cyber-attack vectors for hackers to insert malware, compromise connected technologies, steal patient data, or even jeopardize patient health. Think about the types of devices that can be hacked: defibrillators, respirators, imaging devices, infusion pumps, and wearable devices. The list goes on.
As medical device manufacturers continuously update and maintain their device portfolio, as well as innovate new products, the need to embed cybersecurity and privacy capabilities into the design, build, and maintenance of these devices is fundamental. Furthermore, older medical devices present unique cybersecurity and privacy challenges, as they typically lack the basic cybersecurity features and controls found in newer devices.
The complexity of cybersecurity and data privacy requires a multi-disciplined approach, and not just from a regulatory or technology standpoint. Cybersecurity and privacy programs require input and support from IT, product security, product engineering, research and development, risk management, legal, compliance, and trusted third parties.
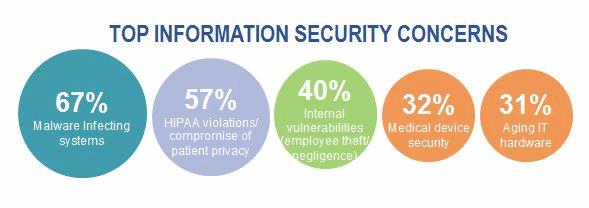
Both manufacturers and providers alike are seeking to benefit from collaboration. This can be seen by the FDA, where the FDA has entered into a partnership with the National Health Information Sharing and Analysis Center (NH-ISAC) and the Medical Device Innovation, Safety, and Security Consortium (MDISS). You will also see that providers have joined the MDCTF (Medical Device Cyber Task Force) in a effort to collaborate among peer organizations. While we continue to focus on sharing and collaboration among both groups, there is still much work ahead and progress to be made. We are though headed in the right direction. Stay the course.
Adopt A One-Policy Mindset
With all of these stakeholders, organizations should adopt a one-policy view of medical device cybersecurity, one and privacy that considers threats to devices, business processes, supply chain, IT, infrastructure, software, and third-party collaborators. Organizations are best served by identifying what is at risk and applying themselves toward prioritizing threats to their product portfolios.
Where To Start?
We advise a “crawl-walk-run” campaign to help guide the development of, or improvements to, medical device cybersecurity and data privacy programs. In the “crawl” stage, organizations assemble a cross-functional team to help define, identify, and prioritize medical device risks. In the “walk” stage, organizations empower teams and fund changes related to governance, communications, threat monitoring, third-party risk management, security, and privacy through design principles, intelligence sharing, and maintenance processes. In the “run” stage, organizations have fully mature asset management capabilities, integrated maintenance processes, a trained and tested coordinated response program, and device-specific training.
Note that device asset management should take into account FDA requirements for Unique Device Identification.
This Is Not Easy
Medical device manufacturers and healthcare providers need to allocate their finite resources to address cybersecurity and data privacy risks in a pragmatic and compliant way. Medical device-specific considerations include:
- Define, document, and prioritize cyber and privacy risk scenarios that are in line with the device type and purpose
- Design and implement cybersecurity and privacy controls addressing prioritized risks
- Introduce and document consistent and secure software development and coding
- Perform penetration testing and vulnerability assessments to identify issues
- Train stakeholders (patients, clinicians, employees, etc.) in methods of medical device protection
- Develop and test coordinated response plans
Thorough cybersecurity and data privacy programs cannot focus solely upon the devices. Your organization must fund, support, and govern a range of initiatives, including:
- Clarify cybersecurity and data privacy program roles and responsibilities
- Design and implement improved maintenance processes related to medical device updates and patches
- Improve vendor risk-management processes and communications
- Introduce improved threat-management capabilities
- Identify the use and transfer of sensitive medical information, and introduce practices that adhere to applicable regulations, such as the Health Insurance Portability and Accountability Act (HIPAA)
- Design and share, as appropriate, intelligence with regulators, trusted third parties, and peers
Medical devices present a unique cybersecurity challenge. The stakes go far beyond patient privacy and enter the realm of patient safety. Lives are at stake. The time to act is now.
About The Author
David Remick is a member of the Healthcare Advisory Practice specializing in Cybersecurity. David has extensive experience delivering successful, IT-related change at global organizations. He leverages his knowledge of accounting, audit, IT, and risk management to help organizations realize their IT, internal controls, governance, security, and privacy related objectives.
